Part 1 : Branch Office configuration:
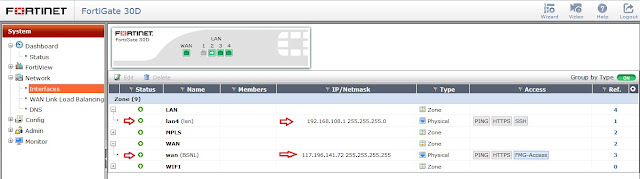
Step 1 - Login to Fortigate 30D and check the details (Branch).
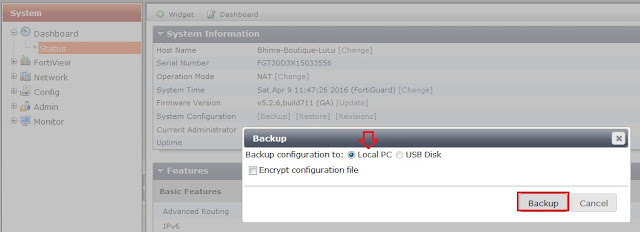
Step 2 - Before changing anything, please take the backup configuration.
Step 3 - Create fortigate DDNS, for accessing through Domain Name.
Dynamic DNS is very helpful if your Internet Service Provider provides you with a DHCP address. Fortinet hosts their own Dynamic DNS servers that is configurable in the GUI. Utilizing their servers will allow you to access your Fortigate via a DNS name that updates automatically when your IP address changes.
After that, check that if it is resolved through online.
Step 4 - Now, we need to create VPN tunnel using IPsec in 30D branch office.
Here, I am choosing custom VPN tunnel. In this section, we need to configure manually.
In the Authentication step, set the HO FortiGate’s IP as the Remote Gateway. Set the same Pre-shared Key that was used for HO’s VPN and Branch VPN.
Step 5 - After creating IPsec VPN, automatically create a VPN interface. Then create zone and add the IPsec VPN interface to this zone.
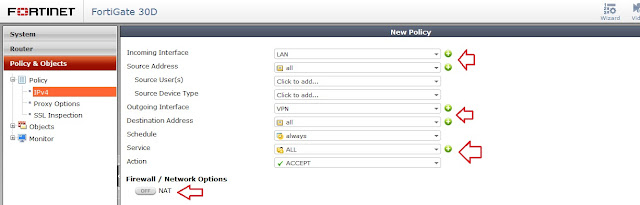
Step 6 - Create a new policy for VPN communication LAN to VPN & VPN to LAN
Step 7 - Create a static route Branch to HO.
Part 2 : Head Office configuration
Step 8 - Before doing, check the details and backup the configuration file.
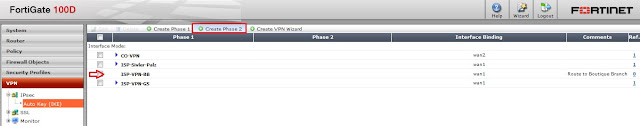
Step 9 - Create IPsec VPN tunnel Phase1 and Phase2.
Here, we are selecting Remote gateway as 'Dynamic DNS' option and enter the Branch DDNS.
Step 10 - Check the interface and create new zone for IPsec VPN, then insert the newly created interface.
Step 11 - Create a new policy for IPsec VPN, LAN to VPN and VPN to LAN
Step 12 - Configure static route HO to Branch.
Step 13 - Finally, we can monitor and check the IPsec VPN connection.
Thats it...










































Thnks and usefull
ReplyDeleteYou have done a great job on this article. It’s very readable and highly intelligent. You have even managed to make it understandable and easy to read. You have some real writing talent. Thank you. expressvpn free trial
ReplyDeleteI am definitely enjoying your website. You definitely have some great insight and great stories. top android vpn
ReplyDeleteThanks for a wonderful share. Your article has proved your hard work and experience you have got in this field. Brilliant .i love it reading. torrenting without vpn
ReplyDeleteI Read your article. Thanks for sharing such beautiful information, You wrote really very well, I really like your blog and the information provided by you. I appreciate your work. If you are interested to know server hosting you can choose the best USA Dedicated Hosting it offers an amazing hosting solution to users.
ReplyDeleteThank you, I appreciate that I getting a lot of good and reliable information from your post. Thanks for sharing such kind of nice and wonderful post. USA Dedicated Server
ReplyDeleteCool and that i have a dandy proposal: Who Repairs House Windows house renovation jobs
ReplyDelete